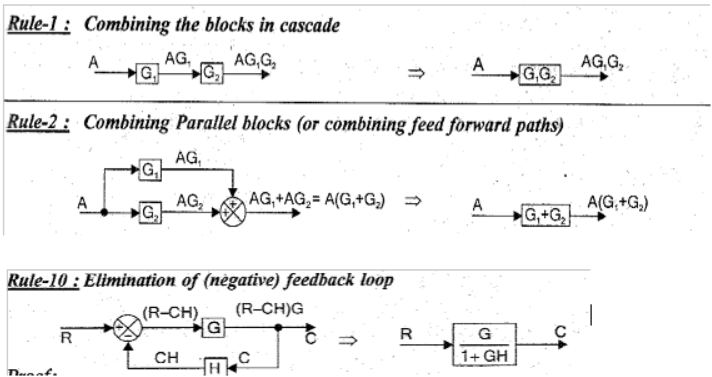
Zeros: Zeros of a transfer function are the values of H(s) for which the transfer function becomes zero.
Geometrically, zeros represent points in the complex plane where the transfer function intersects the x-axis
(real axis).Zeros can influence the system's response by affecting the locations of peaks, dips, or cancellations
in the frequency response.
Poles: Poles of a transfer function are the values of H(s) for which the transfer function becomes infinite or undefined.
Geometrically, poles represent points in the complex plane where the transfer function diverges or approaches infinity.
Poles are crucial in determining the stability and transient response of a system. The stability of a system is directly
related to the location of its poles: if all the poles are in the left half of the complex plane, the system is stable.